Terraform for Network Engineers: Part One
Using Terraform to Manage Network Devices: A Practical Guide for Network Engineers

When I mention to my industry peers that I use Terraform to manage parts of my on-premise network infrastructure, I often get blank stares or a look of surprise. It's understandable — Terraform is usually associated with cloud infrastructure, not on-premise network devices. A quick Google search for "Terraform for Network Engineers" mostly brings up results about creating AWS VPCs, Azure VNETs, or deploying Palo Alto firewalls in AWS. There's not much out there about using Terraform for network devices like routers, switches, firewalls, and load balancers.
In this blog post series, I'll share my experience using Terraform to manage network devices and explain how it can benefit network engineers. While I'm not sure how many parts this series will have, I'll keep each post concise and informative, giving you the essentials to get started. If you have questions or need help, feel free to reach out.
Throughout the series, I'll use Palo Alto Network (Panorama) as the target, but the concepts can be applied to any network device that supports Terraform.
In Part One of this series, we'll cover the following topics:
- Introduction to Terraform.
- Understanding Terraform Terminology.
- Terraform Workflow.
- Deciding if Terraform is the Right Tool.
- Installing Terraform
What you will need to follow along?
To follow along with the examples in this series, you will need the following:
- An instance of of Palo Alto Networks Panorama. Basic understanding of how to configure objects, and firewall policies. (Panorama need not be licensed)
- A MacOS or Linux machine to run Terraform. For the large part, you can use Windows too, but I have not tested it. I will be using MacOS for this series.
- A basic understanding of Git and a GitLab account to store your code, configuration files and state files. I specify GitLab because of some of the integrations it has for Terraform which is missing in GitHub. (The free tier should be enough)
- Your favorite code editor (I will be using Visual Studio Code with the official Terraform extension installed)
- Most importantly, patience and an open mind to learn something new. It is a bit of a paradigm shift to start managing network devices with Terraform, but it is worth it.
So, let's get started!
Introduction to Terraform
Quoting from the HashiCorp website:
"HashiCorp Terraform is an infrastructure as code tool that lets you define both cloud and on-prem resources in human-readable configuration files that you can version, reuse, and share. You can then use a consistent workflow to provision and manage all of your infrastructure throughout its lifecycle."
In this blog, we will explore all aspects mentioned in the quote. We'll define our network devices in human-readable configuration files, version them using Git, and use Terraform to provision and manage our network devices throughout their lifecycle.
Understanding Terraform Terminology
Before we dive into how Terraform works, let us first understand some of the basic terminologies used in Terraform:
- Provider: A provider is responsible for understanding API interactions and exposing resources. Terraform configurations must declare which providers they require so that Terraform can install and use them. In our case, we will be using the
PaloAltoNetworks/panosprovider. - Variables: Variables allow you to parameterize your Terraform configurations. You can use variables to make your configurations more flexible and reusable.
- Resource: A resource is a piece of infrastructure that you can manage with Terraform. Examples of resources on Palo Alto Firewalls will be network objects, services objects, security policies etc.
- Module: A module is a container for multiple resources that are used together. Modules are used to group resources together and make them easier to manage. For example, you can create a module that provisions a network object, service object and a security policy together.
- Output: Outputs are a way to extract data from your Terraform configuration. You can use outputs to get information about the resources that Terraform creates.
- Data Source: A data source is a way to fetch data that is not defined in your Terraform configuration. For example, you can use a data source to fetch would be a network object, service object etc.
- State: Terraform keeps track of the state of your infrastructure. This state is used to map real-world resources to your configuration, keep track of metadata, and improve performance for large infrastructures.
Terraform Workflow
A Terraform workflow consists of mainly four steps:
- Init: This step initializes your Terraform configuration. It downloads the provider plugins and sets up your working directory.
- Plan: This step is a dry run that shows you what actions Terraform will take to change your infrastructure.
- Apply: This step applies the changes to your infrastructure.
- Destroy: This step destroys the infrastructure that Terraform manages.
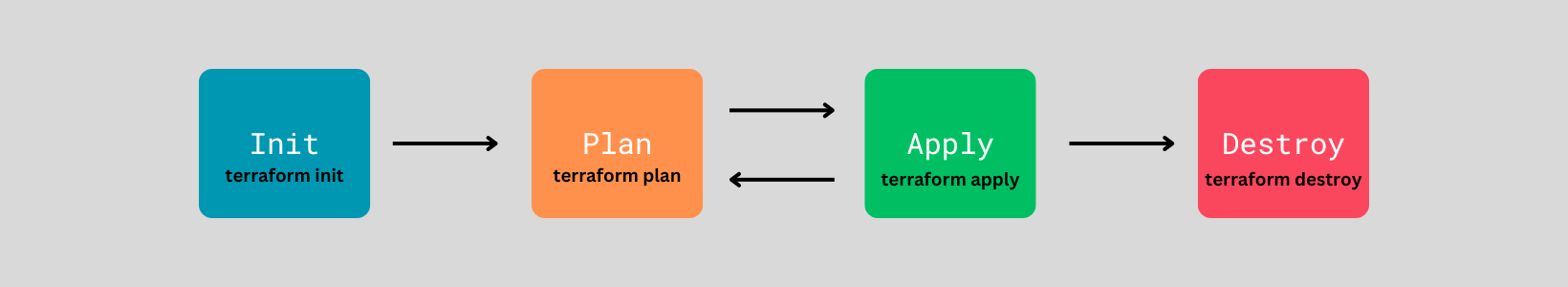
I have deliberately over simplified the workflow here. We will add more context to each of these steps as we go along.
Deciding if Terraform is the Right Tool
When deciding whether to use Terraform to manage your network devices, it's important to base your decision on your specific requirements. Consider these key features and factors:
- Consistent Workflow: Terraform provides a consistent workflow to provision and manage your Network Devices throughout their lifecycle.
- Versioning: Terraform allows you to version your configuration files using Git. This means you can track changes to your Network Devices over time.
- Re-usability: Terraform allows you to reuse your configuration files. You can create modules that define common patterns and use them across multiple projects.
- Common language for Infrastructure and Application teams: Terraform is well known and understand by application teams. This can be a huge benefit in organisations where Infrastructure and Application teams are siloed.
- Learning Curve: Terraform has a learning curve. You need to invest time in learning Terraform and understanding how it works.
- State Management: Terraform keeps track of the state of your infrastructure. You need to understand how state management works and how to handle state files.
- Provider Support: Not all Network Devices have Terraform providers. You need to check if there is a provider available for your Network Device.
- Community Support: Terraform has a large community that provides support and resources. You need to check if there is enough community support for your Network Device.
In my experience with provider support, the most supported and well maintained (take it with a grain of salt) providers for on-premise network devices are from Palo Alto Networks and F5 Networks. I have used both of them and they work great.
Installing Terraform
The process of installing Terraform is straightforward and is already well documented. You can find the installation link below.
Conclusion
In this part, we covered the basics of Terraform, understood some of the basic terminologies used in Terraform, got a Ten thousand foot view of the workflow, and discussed how to decide if Terraform is the right tool for managing your Network Devices. In the upcoming parts of this series, we will dive deeper into each of these topics and learn how to manage Network Devices using Terraform. Stay tuned!





